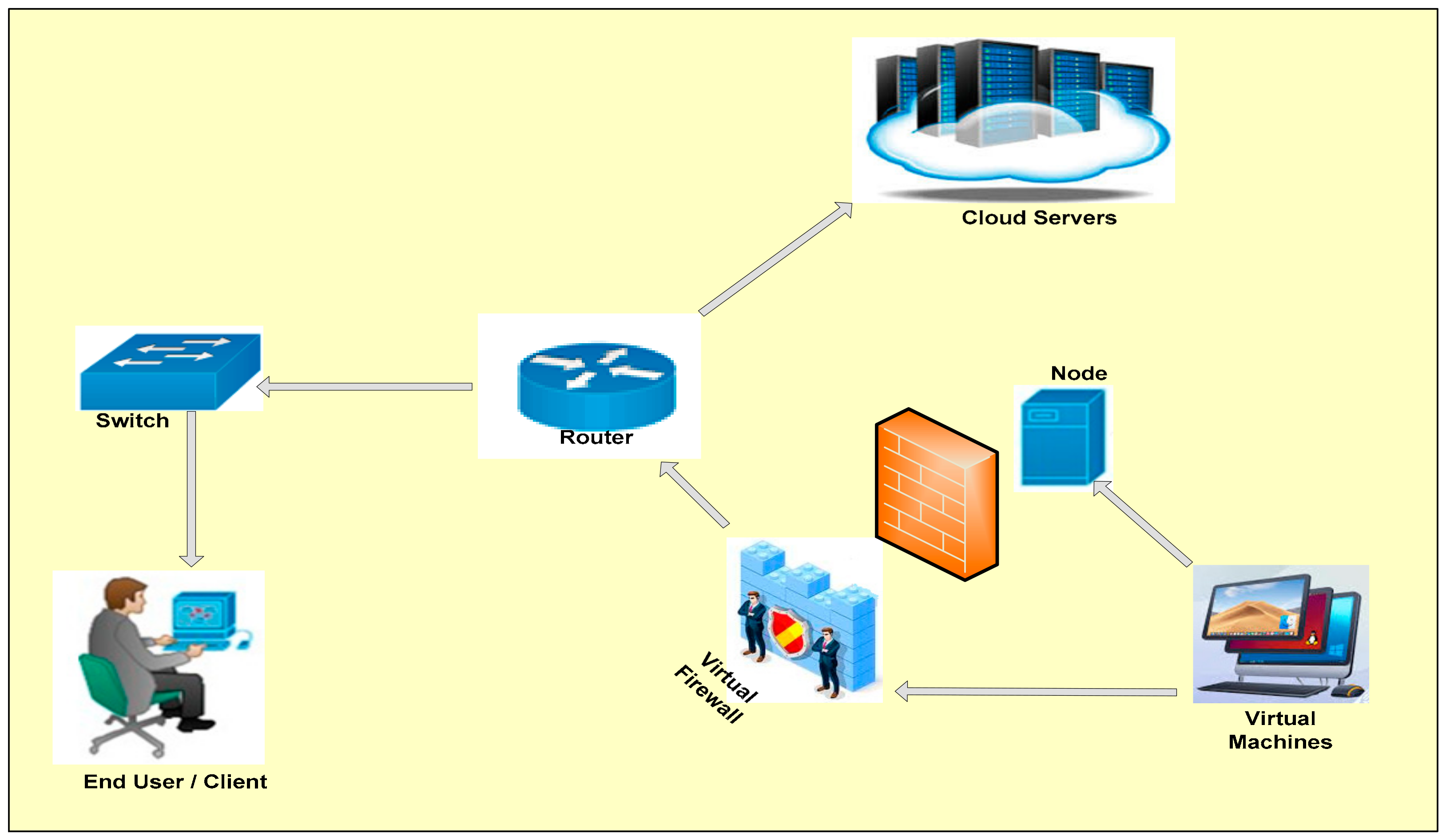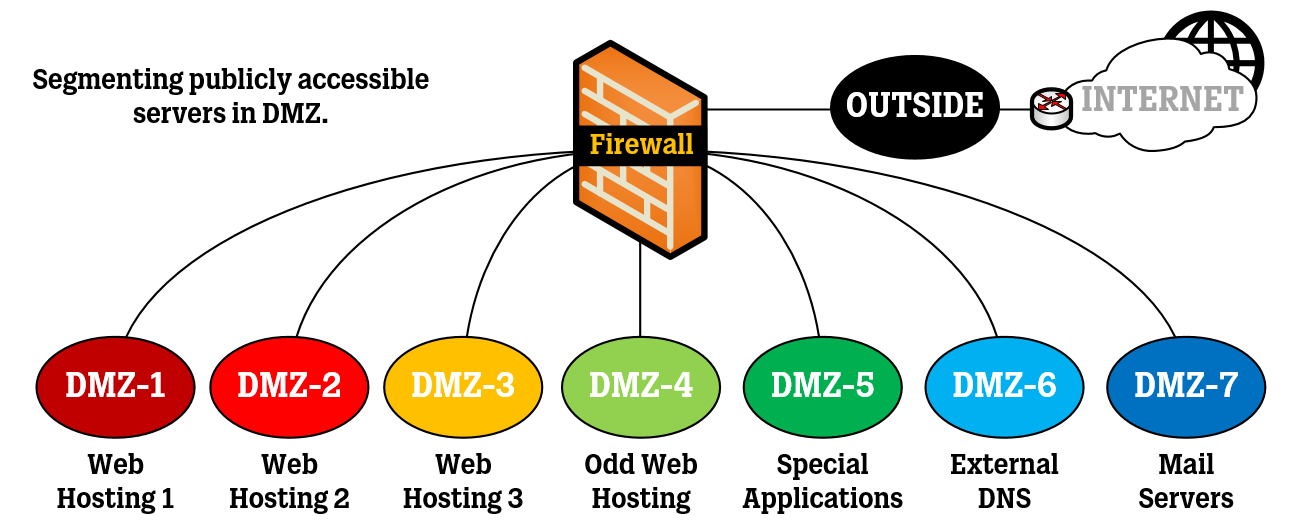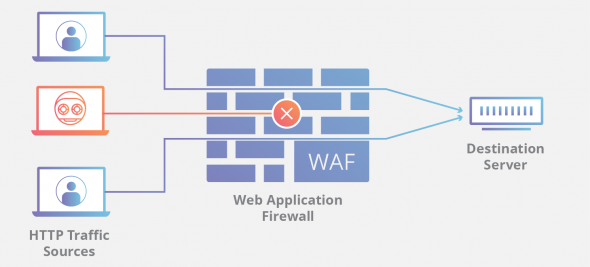
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review
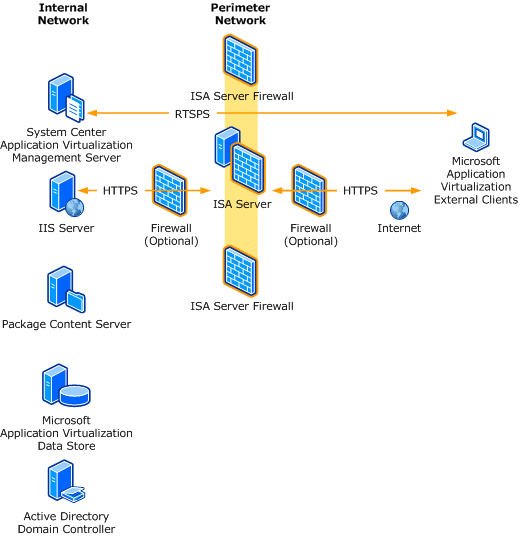
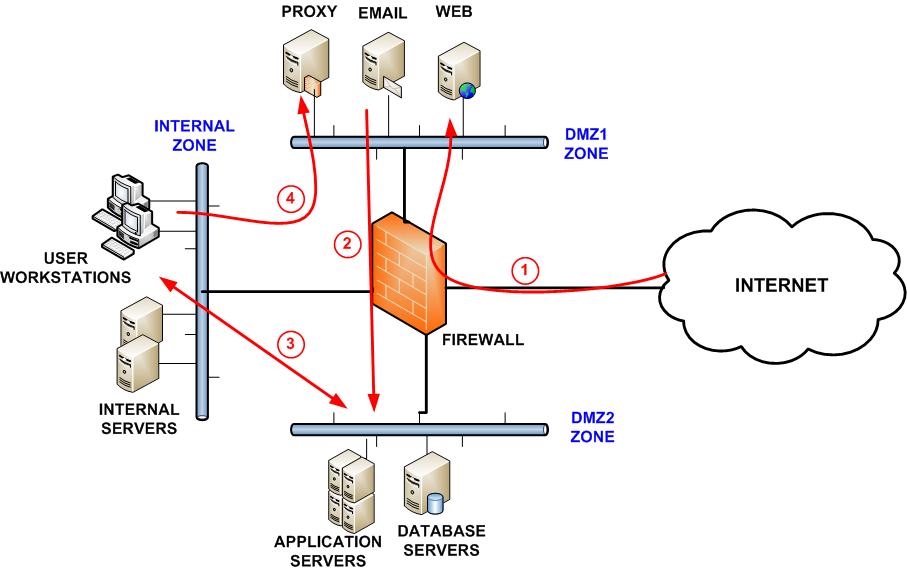
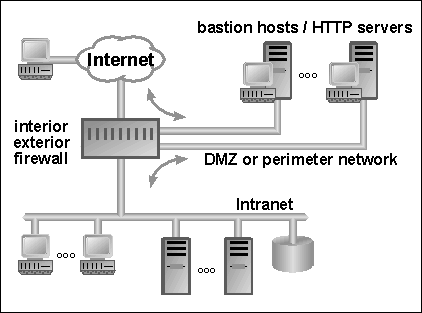
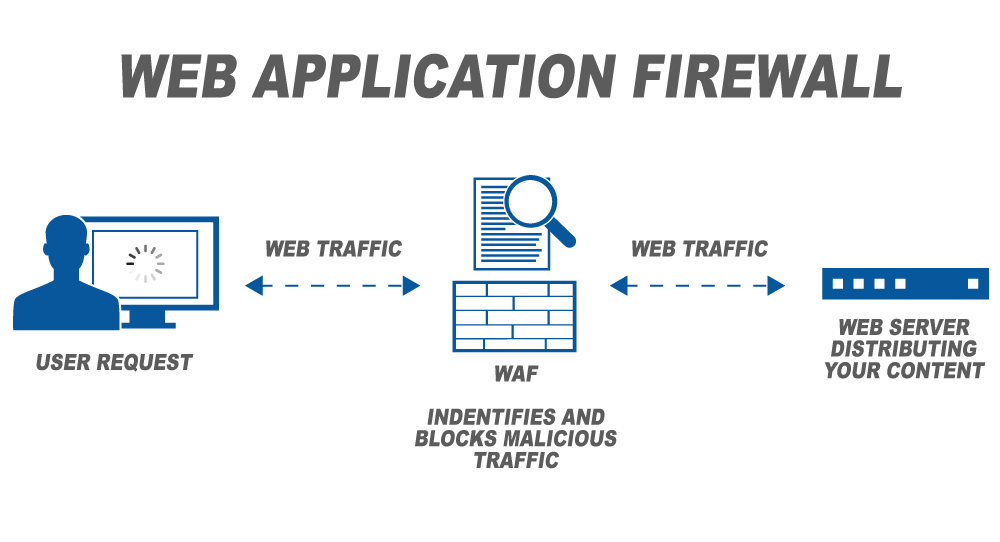
Internet-Facing Server Scenarios for Perimeter Networks - Microsoft Desktop Optimization Pack | Microsoft Learn

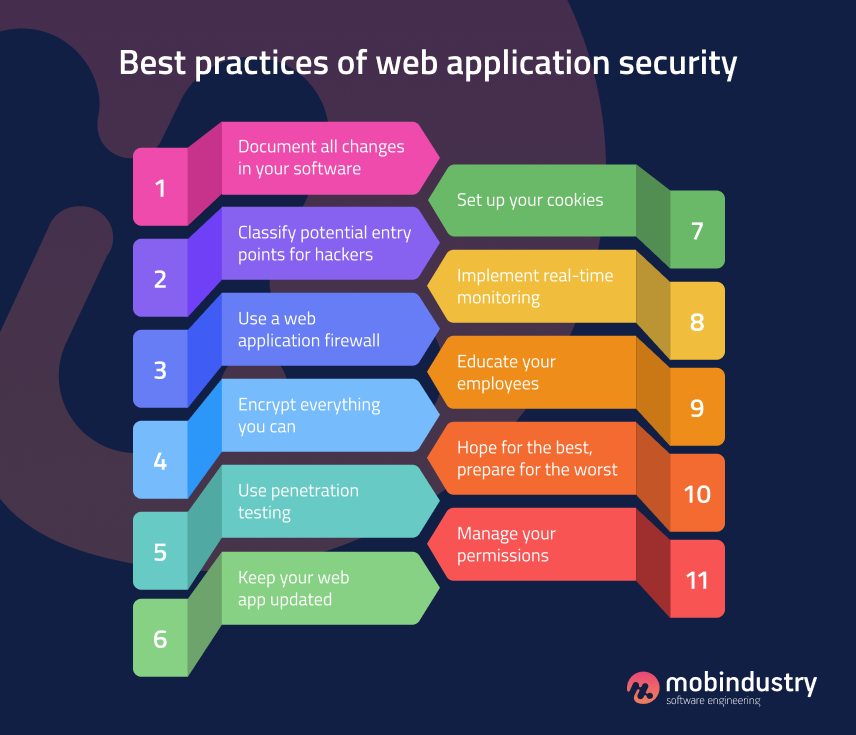
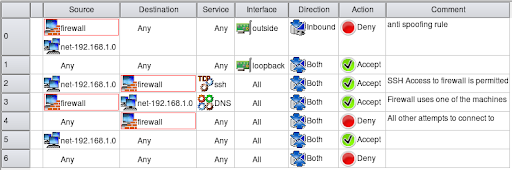
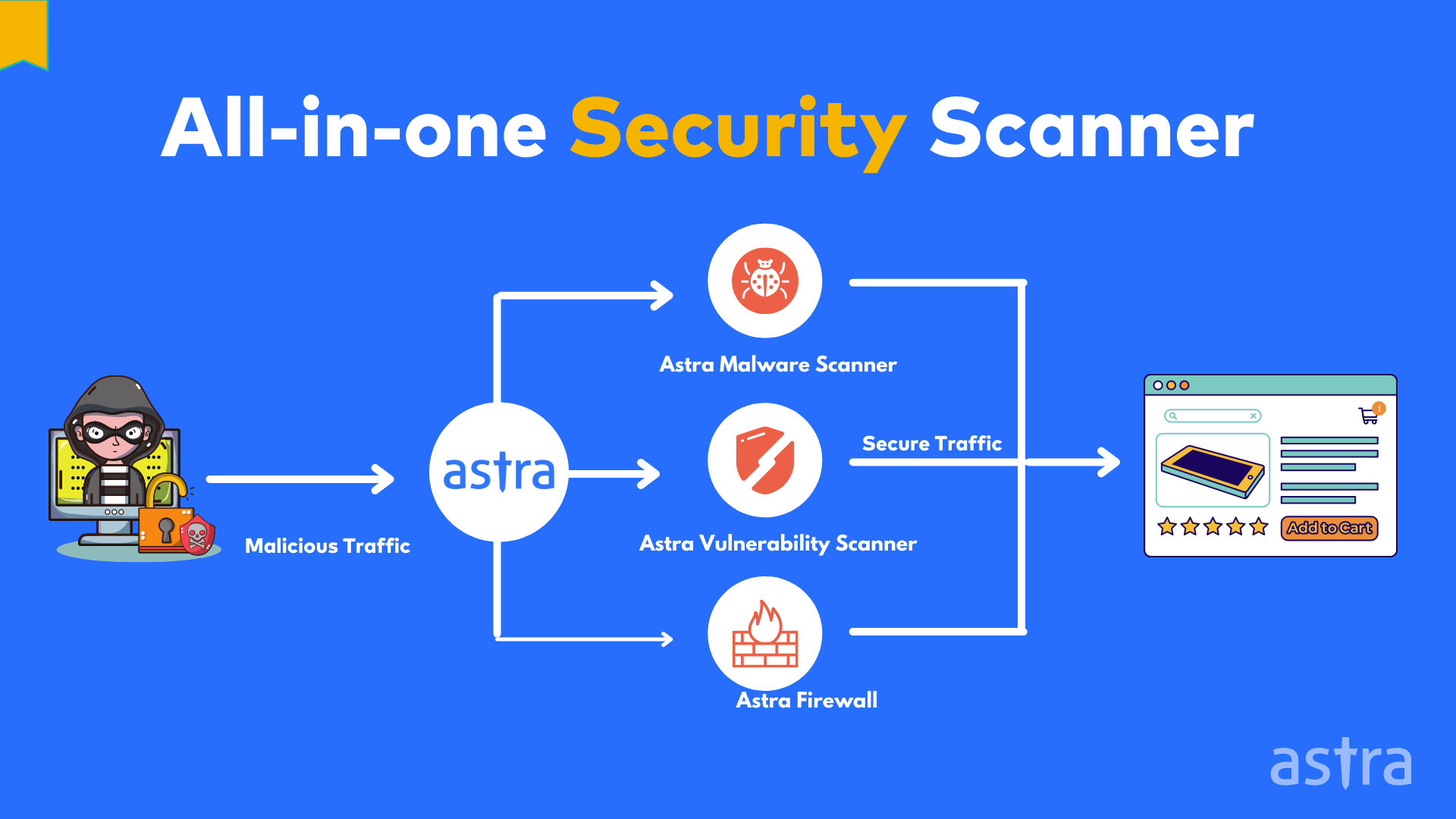
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review
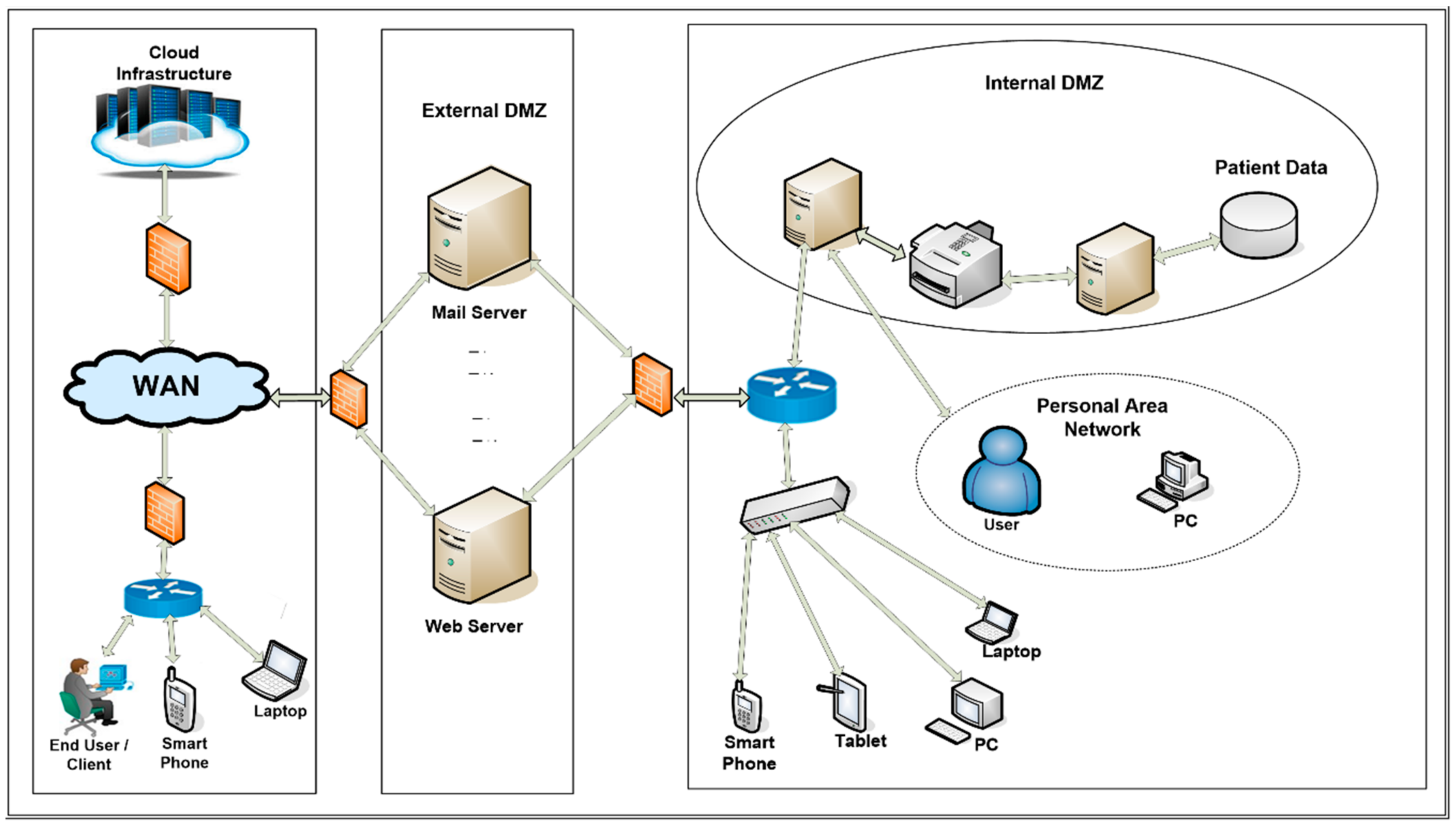
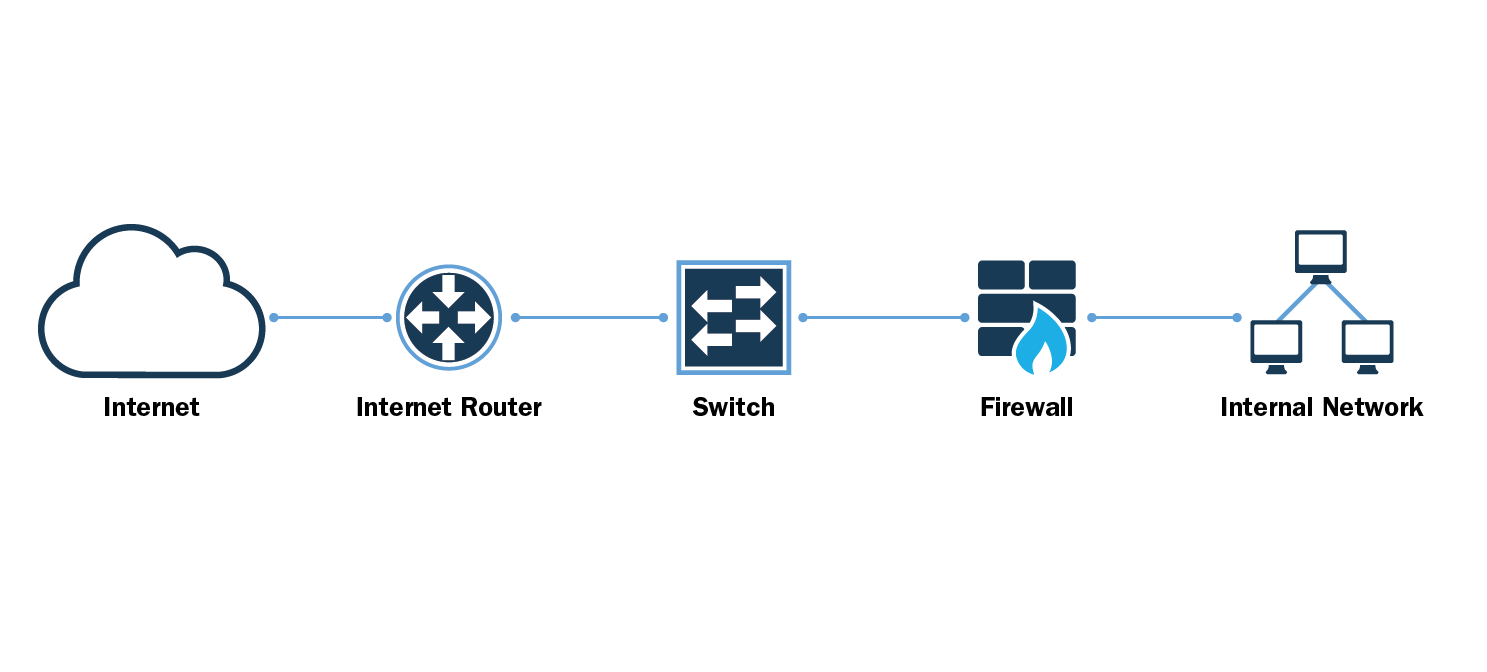
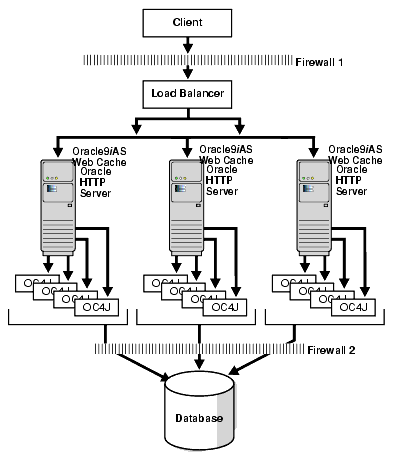
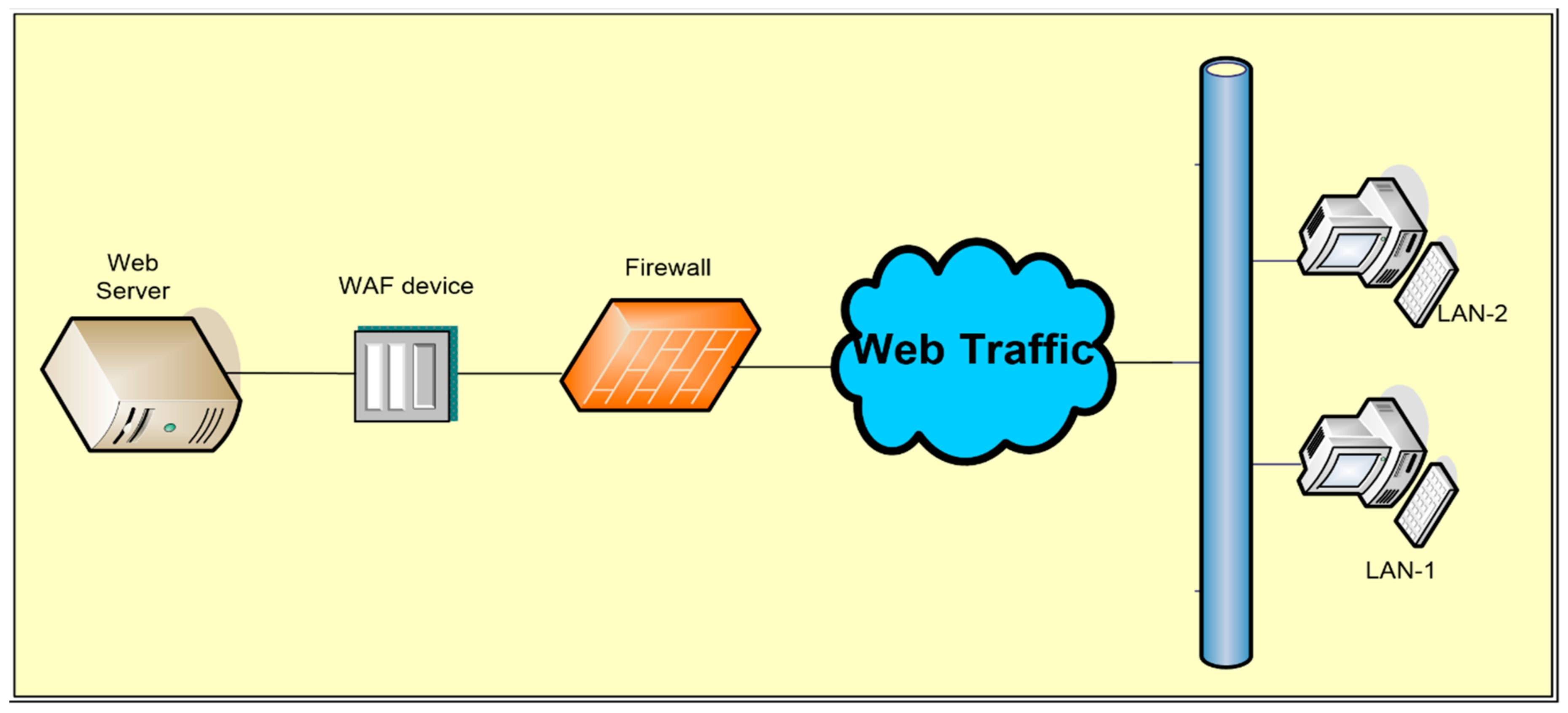
Applied Sciences | Free Full-Text | Firewall Best Practices for Securing Smart Healthcare Environment: A Review