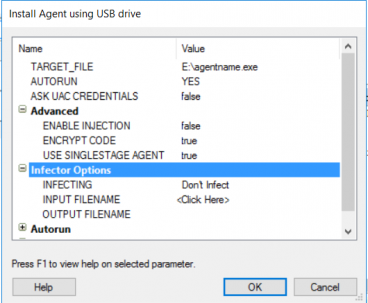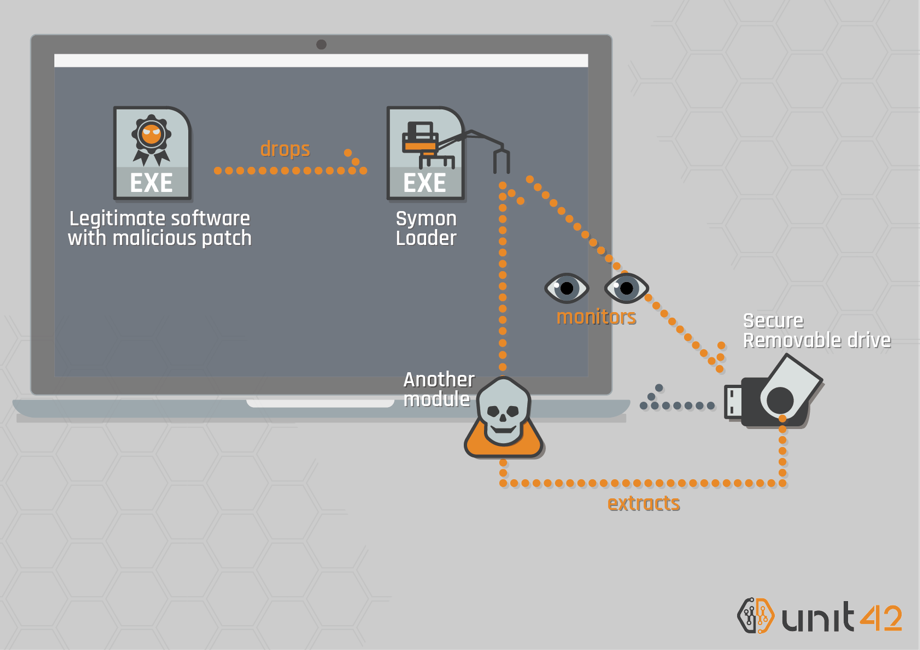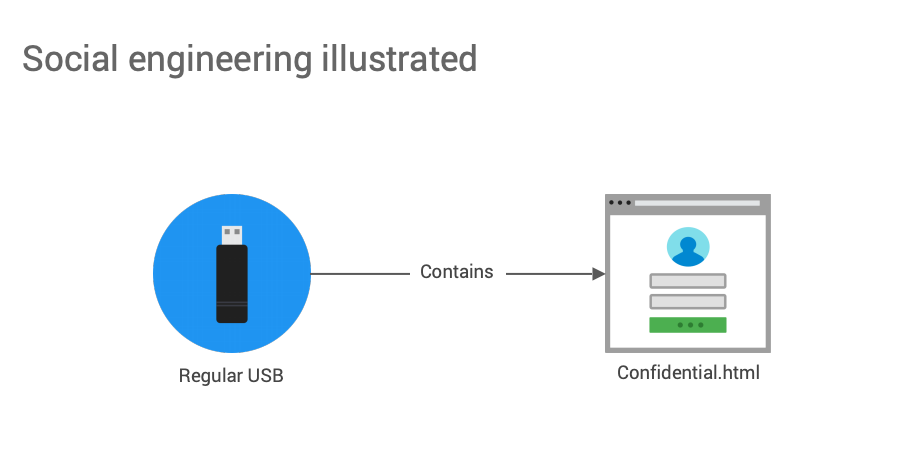
Attacchi informatici con chiavette USB (USB drop attack): come difendersi, anche grazie a Sentinel One.

Kitsap Networking Services, Inc. - USB DROP ATTACK, what do you need to know? There has been numerous threats and hacks that have been conducted in weird and new ways, but what

Iris Classon | Author & programmer on Twitter: "(Not so) Stupid Question 301:What is a candy drop or USB drop attack? https://t.co/dlKPLcdLwk https://t.co/vjCaPvzYse" / Twitter