Symmetry | Free Full-Text | Machine Learning-Based Botnet Detection in Software-Defined Network: A Systematic Review

Surge in Singapore-linked 'botnet drones', used by cyber criminals to hack into household devices: Report - TODAY
Applied Sciences | Free Full-Text | An Adaptive Multi-Layer Botnet Detection Technique Using Machine Learning Classifiers

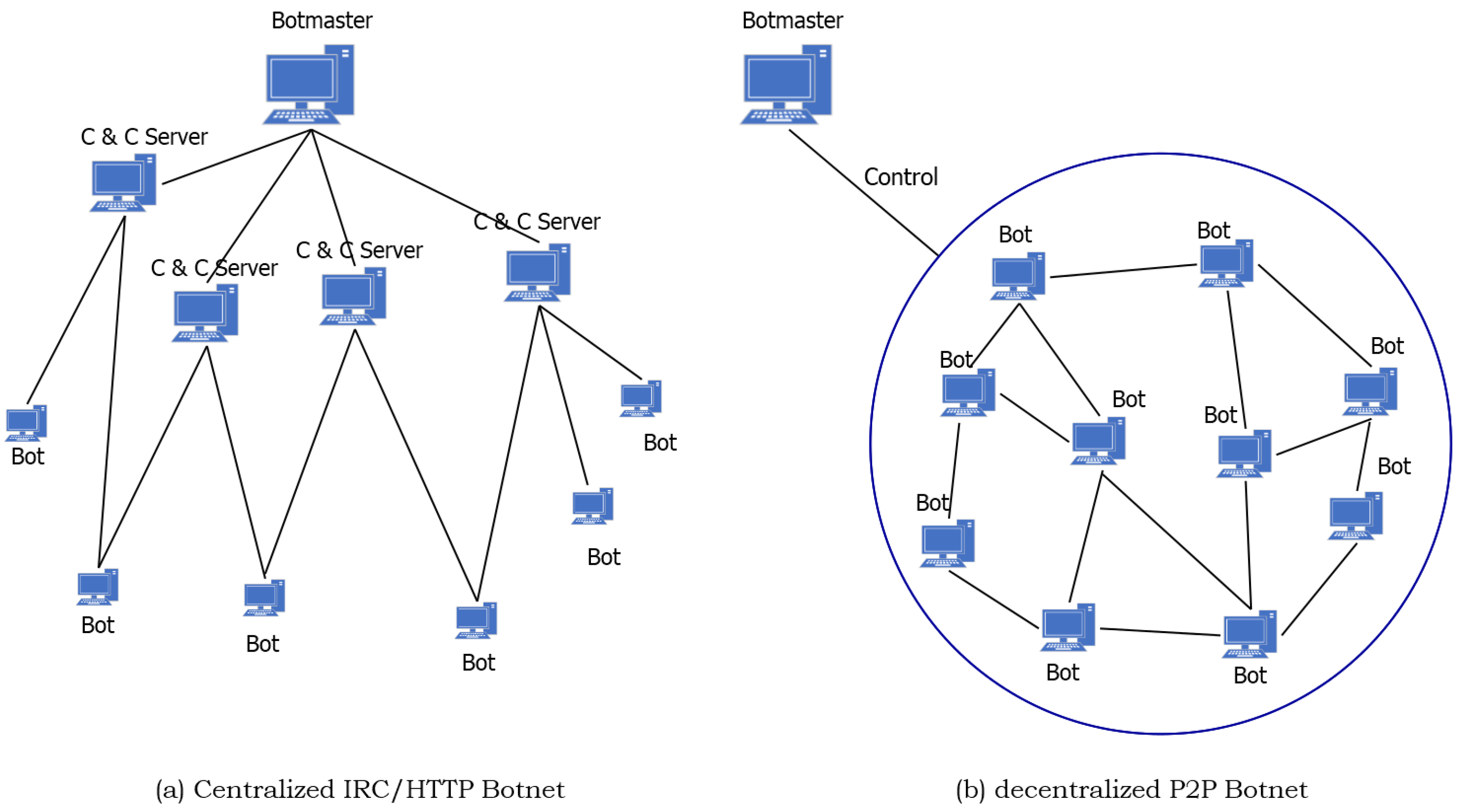
Information | Free Full-Text | A Botnets Circumspection: The Current Threat Landscape, and What We Know So Far

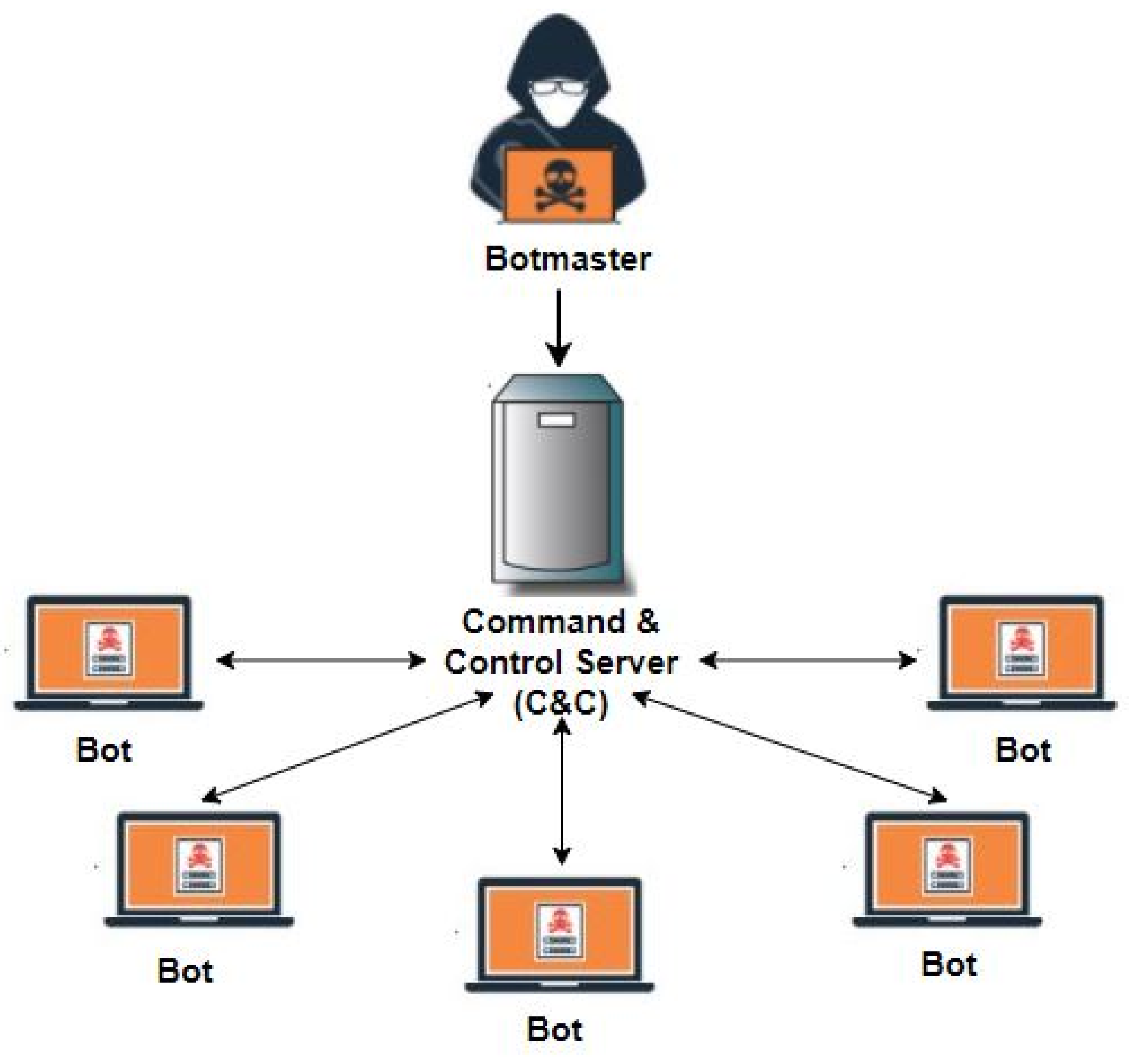
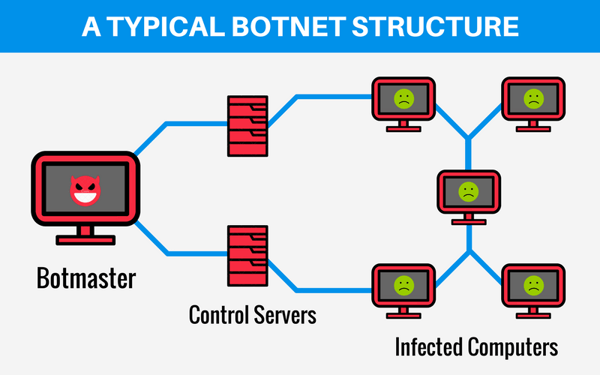
What is a botnet? How are botnets created? How are they controlled? How are bots acquired? What type of attacks are they responsible for? - ppt download

Drones | Free Full-Text | An Intrusion Detection Model for Drone Communication Network in SDN Environment





![What Are Botnets? [+7 Ways to Prevent an Attack] What Are Botnets? [+7 Ways to Prevent an Attack]](https://edgemesh.com/5e3d3268a134a79339be8368/6206efa21e093c005c5bb642_GOlCcrRJTbuYwgQg6opDRU_1cy5F0wjFggQF3_d_x-RlCcHjzSpryH6_WQ8jJQKSEdxvOOyss-EkJqZSVzxoUoRugWQdHeLJhcsyuZzcK6aB3rzf2nFcOuCvg8Kls7IIfzJo-X0cxSRDImO2iqg.png?em-origin=assets.website-files.com)





![Botnet Drone! by Poofdra -- Fur Affinity [dot] net Botnet Drone! by Poofdra -- Fur Affinity [dot] net](https://d.furaffinity.net/art/poofdra/1615251090/1615251090.poofdra_unknown__7_.jpg)